Table of Contents
- Grabify Tools and Their Impact
- Exploring Booter Services
- Understanding DDoS Attacks
- Protecting Against DDoS
- IP Grabbers and Their Usage
- Advanced Booter Panels
Grabify Tools and Their Impact

Using Grabify tools, businesses can detect and log malicious traffic,
enhancing their security protocols against targeted attacks.
Exploring Booter Services

Booters enable controlled stress tests on network components,
providing valuable insights for security assessments. Businesses use these tools to reveal potential weaknesses
and fortify their defensive measures to mitigate potential breaches.
Understanding DDoS Attacks
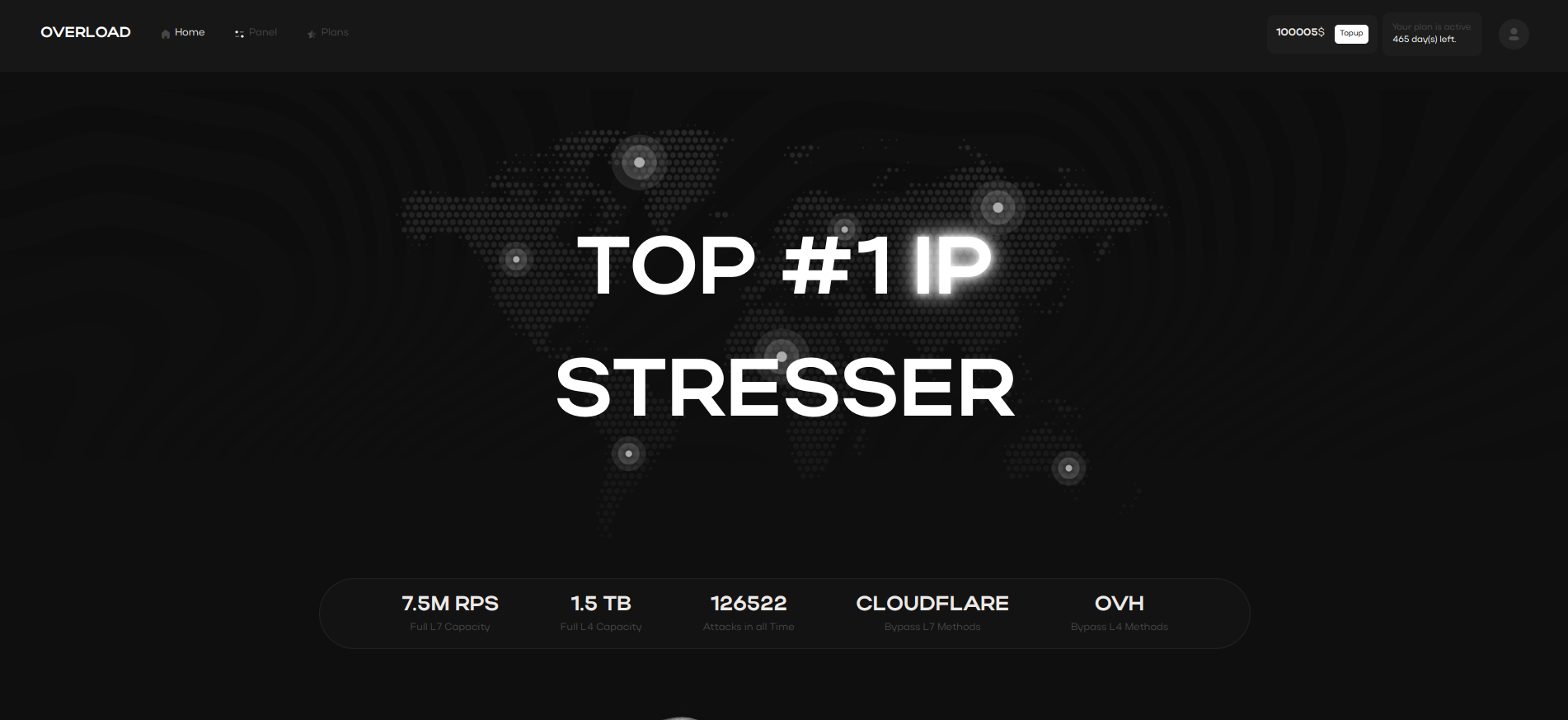
DDoS attacks are a significant threat to online operations, causing service disruptions
and financial losses. Understanding their mechanisms can help businesses mitigate risks and strengthen security protocols.
Protecting Against DDoS

Protecting against DDoS requires layered defenses
and proactive measures. Businesses must secure network infrastructure to mitigate risks.
IP Grabbers and Their Usage

IP grabbers are effective tools for extracting and analyzing network data.
They support cybersecurity efforts by identifying potential threats
and monitoring unusual activity.
Advanced Booter Panels

Booter tools provide seamless access to network testing,
offering user-friendly controls and comprehensive analysis reports.
ddos stresser
ip stresser
xresolver
booter
stresser ip
ddos programs
ddos attack test tool
ddos attack tool
ddos attack service provider
stresserhub
mythical stresser
ddos stresser
anti ddos ovh
stresserst
cloudflare bypass ddos github
bbb booter
